- Messages
- 1,196
- Name
- Red- - - - - - - - - - - - - - - - - -Snappa
- Edit My Images
- No
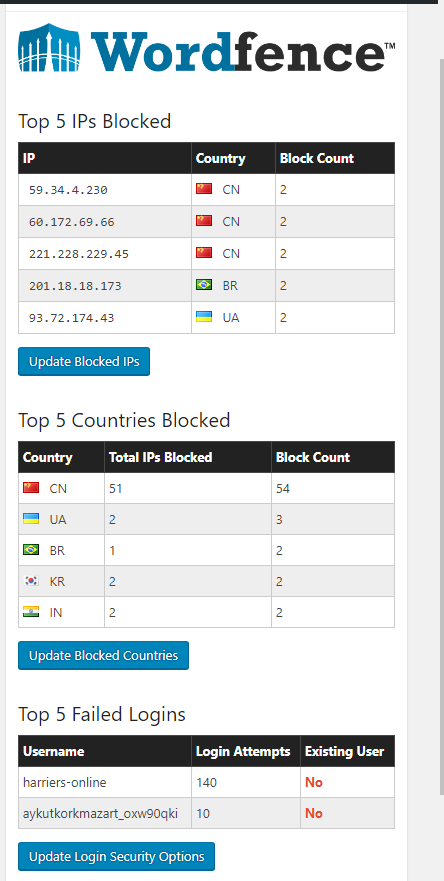
My WordPress website was hacked recently and replaced with a porn site. I cleared the offending site using the TSOhost cpanel.
Before I restore my site from backup I want to know what you guys use do for WordPress security. I thought my 17 character password would be good enough, obviously not.
Before I restore my site from backup I want to know what you guys use do for WordPress security. I thought my 17 character password would be good enough, obviously not.